IoT Explained
06 October 2025
Reading Time: 6 mins
IoT Explained
06 October 2025
Reading Time: 6 mins

Eseye
IoT Hardware and Connectivity Specialists
LinkedInAn IMEI (International Mobile Equipment Identity) number is a unique 15-digit code that identifies every cellular-connected device worldwide. Think of it as your IoT hardware’s digital passport. You’ll need it to check device status, unlock mobile network operator (MNO) services, and ensure your IoT device is authorized on global networks.

Every cellular IoT device — from smart vending and EV chargers to medical equipment and asset tracking — comes with a unique IMEI number. It’s not random: it’s a global standard used by mobile network operators (MNOs) and regulators to identify and authenticate devices. Unlike a SIM card, which links to a subscription, the IMEI links directly to the device hardware itself.
That makes the IMEI invaluable for enterprises because it enables:
In short: if an IoT device connects to a mobile network, its IMEI is the passport that gets it through the gate.
An IMEI is usually 15 digits long, structured into segments:
For example: 356938035643809.
This structured approach ensures no two devices share the same IMEI.
Why does it matter? Because mobile networks trust IMEIs to validate devices. Without a valid IMEI:
For IoT, this becomes even more critical. Imagine deploying thousands of connected sensors worldwide. IMEIs provide the traceability and compliance needed to ensure every device can operate securely and at scale.
IMEI isn’t the only identifier. Some networks, especially in the US, use MEID (Mobile Equipment Identifier).
While some legacy CDMA networks used MEID, today IMEI is the universal standard and the one that matters for virtually all modern IoT devices.
Unlike consumer phones, IoT devices often don’t have screens, so you’ll need to use other methods:

In IoT, the IMEI isn’t just an identifier — it’s a control point for security, compliance, and lifecycle management. Enterprises rely on IMEIs for several reasons:
Device onboarding at scale: When activating thousands of devices across different regions, IMEIs provide a reliable way to register and validate each unit.
Device status: IMEIs inform you whether or not the SIM is linked to a device.
Network authorization: Mobile operators use IMEIs to decide whether a device is permitted to connect. Without a valid IMEI, your IoT device won’t get service.
Fleet management: Enterprises track IMEIs to monitor deployed devices, manage warranties, and ensure hardware accountability.
Security compliance: IMEIs are logged in GSMA and carrier databases, helping enterprises prove their devices are genuine and compliant.
Fraud prevention: If devices are stolen in transit or during deployment, IMEIs can be blacklisted to block unauthorized network access.
Diagnostics and support: Technical teams often request IMEIs when troubleshooting connectivity issues or escalating with carriers.
In short: the IMEI helps enterprises keep control of sprawling IoT estates. Without it, there’s no way to ensure that every device in the field is real, authorized, and functioning as expected. In many IoT platforms, including API-driven ones like Infinity, the IMEI acts as the lookup key for retrieving device details, activity logs, and connectivity status automatically which eliminates the need for manual checks.
You can enter your IMEI into online databases provided by MNOs or GSMA services. These checks reveal if your device is:
For IoT, this reduces costly deployment errors. Knowing the status upfront prevents dead-on-arrival devices in the field.
Eseye’s Infinity Connectivity Management Platform shows your device status and signals whether the SIM is Linked or Unlinked to the device:
With our enterprise-grade IoT management APIs, IMEI checks can be automated at scale to let you instantly verify thousands of devices across multiple carriers and regions in one request.
Alongside IMEI, you may see IMEISV (International Mobile Equipment Identity Software Version). This adds two digits to indicate the device’s software version.
Why it matters:
IMEISV keeps devices accountable, not just at the hardware level but also in terms of software integrity.
In the enterprise world, blacklisting isn’t about losing a single handset — it’s about preventing compromised, counterfeit, or stolen devices from entering your IoT estate. A blacklisted IMEI is flagged in global or carrier databases as unauthorized. Once listed, that device cannot connect to most mobile networks.
For IoT leaders, that means blacklisting protects your deployment from risk, fraud, and regulatory non-compliance.
When deploying thousands of devices worldwide, even a handful of blacklisted units can derail operations. Imagine rolling out smart meters, medical devices, or logistics trackers only to discover some can’t connect because their IMEIs are invalid or blocked. That translates directly into wasted time, sunk costs, and lost trust.
By checking IMEIs before devices are activated, enterprises can:
Instead of manual lookups, enterprises use IoT connectivity management platforms and APIs to automate blacklist checks at scale.
Lifecycle monitoring: Continuous checks flag devices that become blacklisted after deployment.
Programmatic verification: APIs query carrier and GSMA databases in real time.
Batch validation: Enterprises can upload IMEI ranges to confirm status before shipment or activation.
If devices are incorrectly blacklisted, resolution usually involves:
Proactive validation at onboarding avoids most of these headaches. We recommend that enterprises build blacklist checks into their IoT deployment workflows from day one.
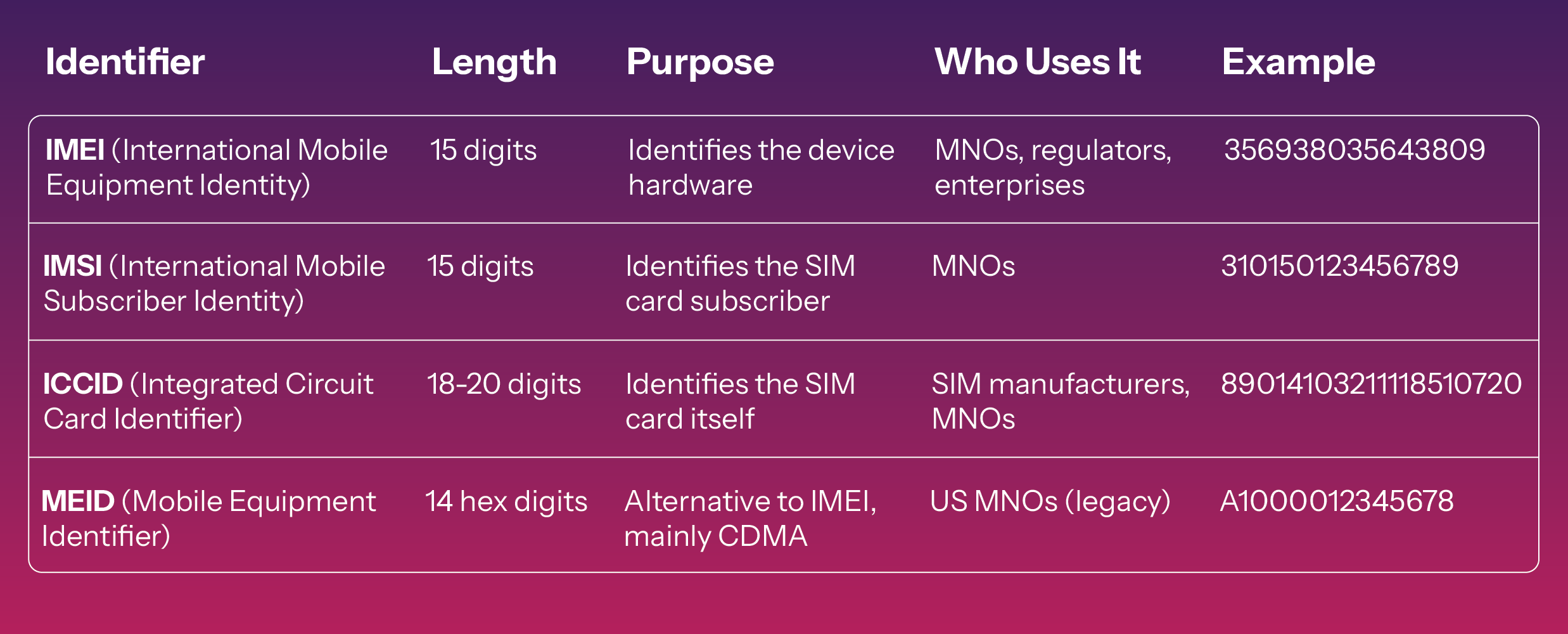
This table clarifies a common source of confusion. IMEI = device, IMSI = subscriber, ICCID = SIM, MEID = legacy device ID.
No. Every IMEI is designed to be unique. Duplicate IMEIs usually indicate tampering or counterfeit devices.
Enterprises should manage IMEIs securely within trusted systems such as IoT connectivity platforms and APIs. Sharing IMEIs publicly creates a risk of misuse.
IMEI identifies the device hardware. IMSI identifies the subscriber on the SIM card. Together, they tell a network who you are and what you’re using.
In most regions, altering or “spoofing” an IMEI is illegal. Enterprises should avoid tampering and instead resolve connectivity issues via authorized channels.
Any IoT device with cellular connectivity should have an IMEI. For massive IoT deployments, tracking IMEIs is essential to manage connectivity, compliance, and lifecycle.
At first glance, an IMEI looks like just another technical code. In reality, it’s a cornerstone of mobile security, compliance, and device management.
For individuals, it protects your phone and unlocks mobile services. For enterprises, it underpins IoT at scale — tracking, authenticating, and securing entire fleets of devices worldwide.
At Eseye, we help businesses put IMEIs to work. They’re more than consumer identifiers: they’re the key reference point in how enterprises query, monitor, and safeguard IoT deployments. Combined with intelligent connectivity management, IMEIs give you the foundation to scale IoT with confidence.
In a connected world, an IMEI isn’t just a number. It’s your device’s ticket to secure, resilient connectivity.
Predictable performance is the key to IoT success. Let our experts test your device for free. Receive a free trial IoT SIM trial kit and speed up your IoT deployment with expert insights and seamless connectivity.