IoT Explained
16 February 2021
Reading Time: 3 mins
IoT Explained
16 February 2021
Reading Time: 3 mins

Paul Marshall
Founder & CCO
LinkedInIs the internet your weakest link? Here’s how Virtual Private Networks (VPNs) can secure your IoT data in transit, plus advice on what to look for in your end-to-end IoT security.
Find out how to secure your IoT from device to cloud in this whitepaper.
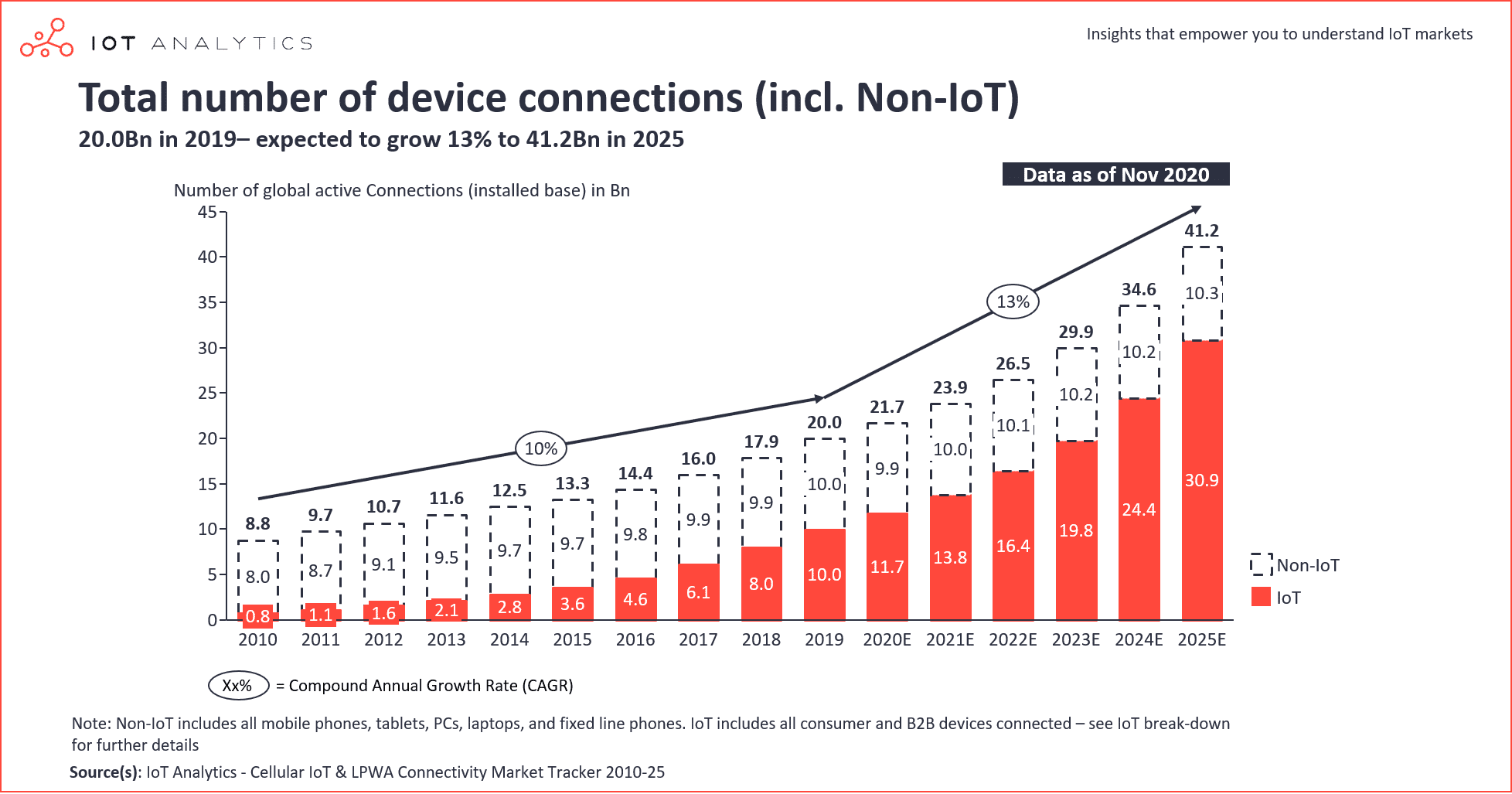
By the end of 2020, there were 21.7 billion active connected devices worldwide. For the first time, the number of IoT connections (such as smart home devices and industrial equipment) exceeded the number of non-IoT connections (such as smartphones and computers). The demand for IoT continues to grow, with the number of connected IoT devices estimated to reach nearly 31 billion in 2025.
The pandemic has magnified the spotlight on the potential of the Internet of Things. IoT applications for smart homes, remote working, industry, and health and safety in business, factories, retail, and hospitality create enormous opportunities for improving efficiency, productivity, and quality of life.
Unfortunately, as IoT grows, so does the potential for cybersecurity attacks – another trend that has accelerated during the pandemic.
Analysis at the end of 2020 showed that 63% of companies reported an increase in cybersecurity attacks during lockdown, while the FBI estimates that, on average, IoT devices in the US are experiencing 4000 cyberattacks every day. The size of the attack surface is expanding rapidly, offering hackers an ever-increasing supply of new vulnerabilities to exploit.
Compared to cellular connectivity and private networks, the internet can be like the wild west.
Cellular connectivity is based on GSMA standards and is covered by stringent regulations and quality of service requirements, including data encryption. SIMs are highly secure integrated circuits with strong authentication mechanisms. They can be embedded into devices or integrated onto a chip for even stronger tamper-proof security.
With private networks, organisations have the ability to deploy the levels of security that they need.
With the internet, it’s a different story. Using publicly-available infrastructure saves resources – and may be essential with IoT devices spread throughout the world. But the way in which IP data packets are routed across large networks opens up vulnerabilities to attacks on the data in transit.
For example, a machine on a network might impersonate another, is a type of attack known as spoofing. Another type of attack – sniffing – involves a hacker eavesdropping on communications between two other parties. A combination of snooping and sniffing enables a hacker to hijack an established communications session and impersonate one of the parties involved.
There are countless examples of hackers intercepting IoT connections to steal and sell intellectual property and personal data. Others have recruited unsecured IoT devices into vast botnets to use in DDoS (Distributed Denial of Service) attacks.
But many IoT devices are constrained by size and power, which limits the security features they can employ, such as data encryption and the latest secure network protocols. Other measures are needed to provide the end-to-end security that can protect the devices – and ultimately the consumers and companies that own, operate, or sell them.

The best way to protect your data on the internet is to use a Virtual Private Network (VPN).
The Internet Engineering Task Force (IETF) created Internet Protocol Security (IPsec), a suite of IP protocols that provide security services at the network level. IPsec is based on advanced cryptographic technology that provides secure data authentication, integrity, and privacy on large networks.
IPsec provides secure tunnels between two peers, such as two routers. Configuration rules determine which data must be sent through the tunnels. By encrypting and authenticating the traffic at the IP level, IPsec ensures secure networking both for applications with good security mechanisms and those that don’t have adequate security provision.
Another advantage is that the IP addresses of the devices and systems behind each VPN router are hidden from the wider environment, preventing these addresses from being tracked. Hackers cannot find out where data originated from and cannot send unauthorised data to the devices.
In some situations, a VPN isn’t required. This is usually if your data is already encrypted at the device level or in one of the IoT messaging protocols, such as MQTTS, COAP or DTLS. Some cloud services, such as AWS IoT core or Azure IoT hub, use their own security methods, including data encryption, instead of VPNs.
In many situations, however, we recommend that a VPN is implemented to secure your internet communications.
Securing an IoT deployment requires a comprehensive, end-to-end approach that covers all the components of a solution from the physical devices and sensors to the systems that process and respond to the data.
As a specialist IoT connectivity provider, Eseye offers a range of IoT security measures, from building in security during device design, to platforms with sophisticated monitoring tools that alert you to events such as unexpectedly high data usage or a SIM fitted into a different device.
We can provide enterprise-grade VPNs with advanced encryption and authentication features to protect your data as it traverses the wild west of the internet.

Paul Marshall
Founder & CCO
LinkedInPaul is one of Eseye’s co-founders. With a background in senior design engineering, Paul’s focus is on ensuring his development, operations and support teams deliver solutions that work faultlessly in the field.
Paul was co-founder of CompXs, with Ian Marsden, and developed the world’s first IEEE 802.15.4 radio. Before CompXs, Paul was in senior radio design at Philips.