Policy-based networking
Streamlined, tailored connectivity
Our policy-based networking approach uses a software defined network (SDN) designed to optimise IoT connectivity across an estate and deliver the precise requirements of customer’ devices.
Software Defined IoT Networks
Next generation IoT networking.
Rapid device onboarding
Our network enables devices to be rapidly onboarded. Your device policy and rules are easily turned into networks settings
IoT security
Segmented from other traffic, we provide end to end security, from the SIM, network and into the cloud
Optimised for IoT devices
Accommodates your application requirements. The network settings and controls ar configured to ensure your device just works!
Connectivity Without Compromise
Demand the best for your IoT project
We choose not to compromise and neither should you. We don’t use shared networks because we believe for IoT to be successful it must run on a network that is designed just for IoT. Other network solutions just can’t deliver the quality of service and configuration our customers expect.

Enhanced traffic visibility
This means we have greater visibility of the traffic. We are able to provide deep inspection of packets, trace and alert customers should we find something we need to draw your attention to. We can then agree to action changes and or corrective measures.

Security policy configuration
There is a fine balance in applying security rules to networks and devices. Underspecify and your data is easily compromised. Over-specify and the onboarding of devices turns into a big headache with devices being rejected, so our network and device experts are on hand to advise and optimise security.

Data sovereignty
We use policy-based connectivity to keep you compliant with the latest data sovereignty rules.
We ensure your data is secure and kept in the right geographies to avoid those regulatory fines that can be as much as 4% of your global turnover.
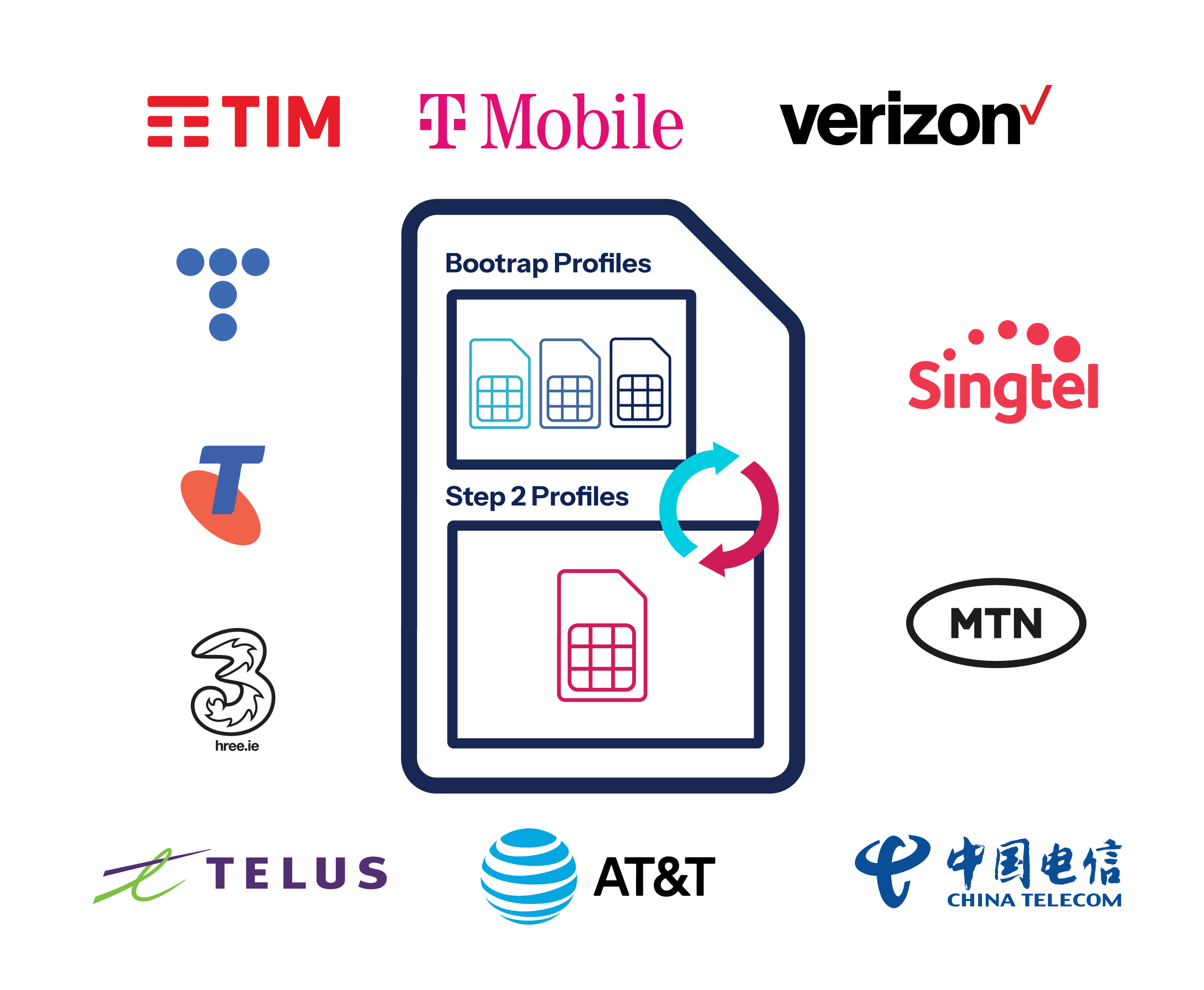
Regional breakouts
We are connected to the key MNOs and cloud providers to support localised connectivity.
Having this key infrastructure in all the right places means you can plan your business growth on market attractiveness rather than where the right infrastructure is.

Mission control for IoT Connectivity.
Today and tomorrow.
Find the perfect Infinity package for your business today. Changing needs? Simply move to a different package.